May 04, 2023
Discovering the Dark Web: A Guide to Monitoring Its Activities

Monitoring the dark web is a service that aims to prevent identity theft by allowing users to track their private data, logins, passwords, and documents. These types of incidents often occur due to data being stored carelessly in unprotected or improperly configured cloud storage, such as AWS S3 buckets. In order to combat this issue, businesses must become much more proactive in their response.
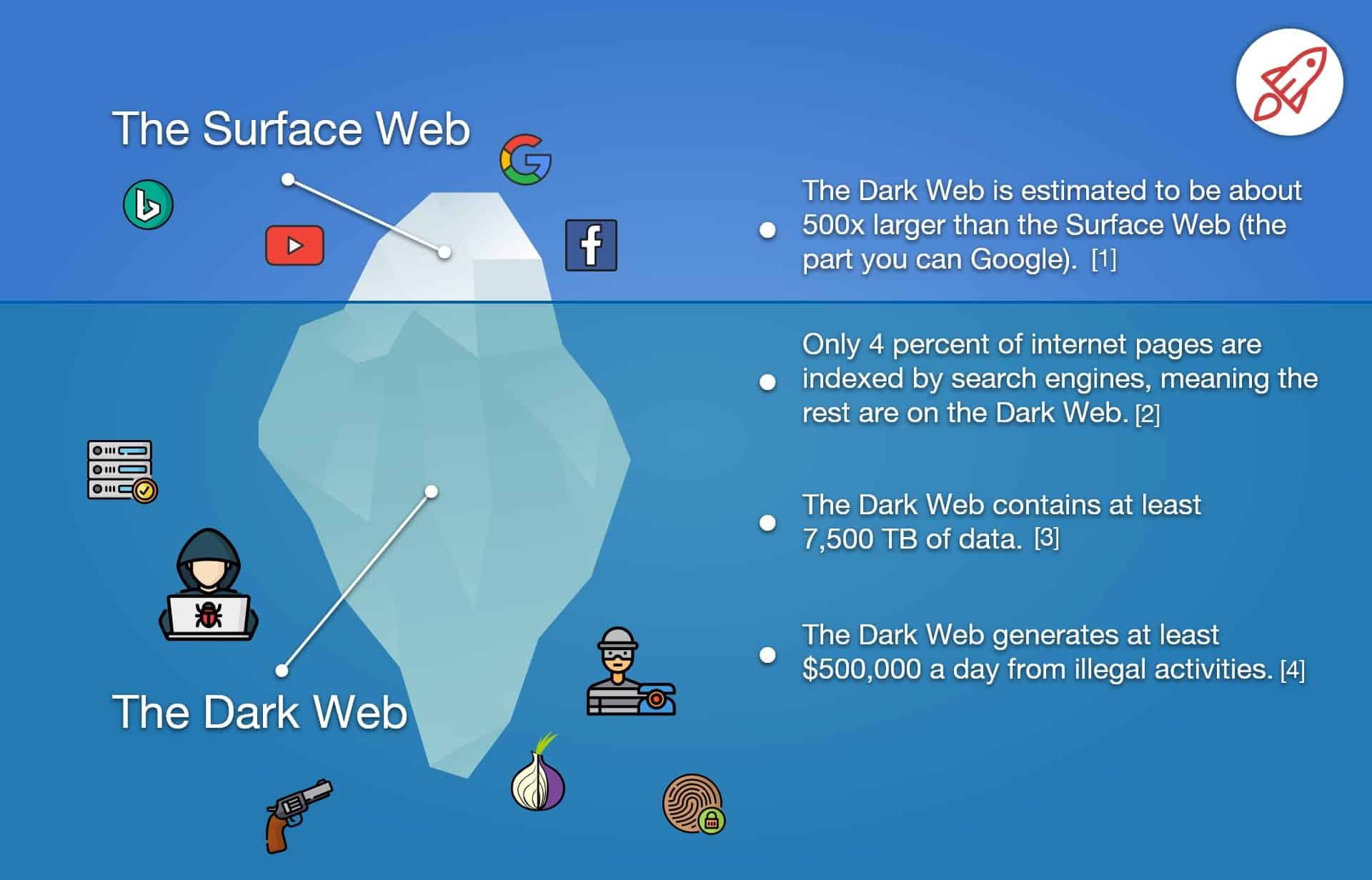
Monitoring the dark web is a crucial process that cannot be ignored, especially considering the magnitude of the problem. Over 21 million corporate accounts have been reported to belong to the dark web, highlighting the need for organizations to take action. Dark web monitoring involves the search and tracking of your organization's information on the dark web. It is important to note that there is also a term called Surface Web or just Surface that should be familiar in the context of dark web monitoring.
Monitoring the dark web has become crucial for businesses and organizations looking to protect their sensitive data and prevent cyber attacks. It is important to recognize that the dark web is a hidden layer of the internet that is not accessible through traditional search engines and requires specialized software to access. However, it is a breeding ground for cyber criminals who use it to buy and sell stolen information, malware, and other illegal goods. By monitoring the dark web, businesses can stay ahead of potential threats and take preventive measures to secure their networks. Remember, you can't defend against threats you don't know exist, and the dark web is a prime example of this.
Monitoring the dark web allows businesses to gain insight into threats that may not be detected by conventional security measures. This term refers to a section of the internet that requires authentication to access, ranging from password-protected websites to highly secure corporate data centers that house valuable data and intellectual property. By continuously monitoring the dark web and responding quickly to any exposed assets or identities, these tools help to reduce the window of opportunity for cybercriminals to exploit confidential information. This can prevent further information leaks and protect sensitive data from falling into the wrong hands.
As an experienced copywriter, I can provide a rewording of the topic "Monitoring dark web" in English. The dark web refers to a portion of the internet that is not indexed by standard search engines and is often associated with illegal activities. It is important to monitor the dark web to prevent cyber threats and protect sensitive information. Various tools and services are available to monitor the dark web for potential threats, such as data breaches or illegal activity. Monitoring the dark web can help individuals and organizations stay informed about potential dangers and take proactive measures to safeguard their online presence.
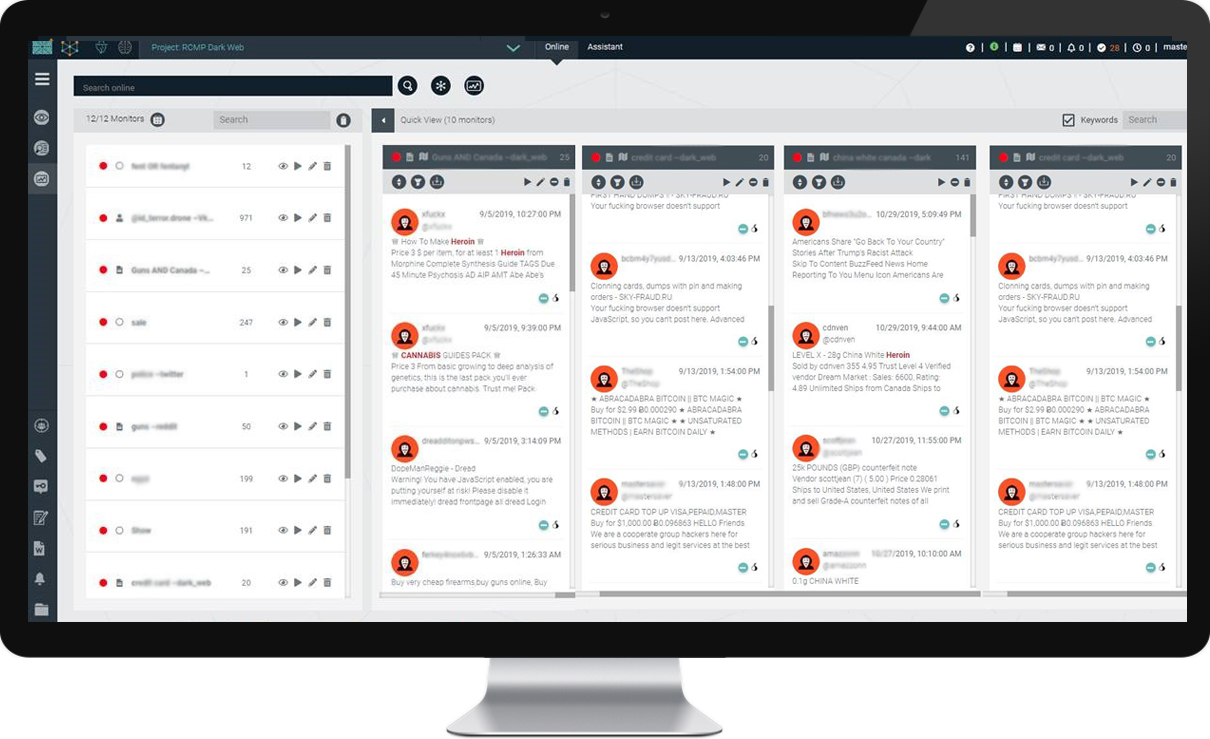
DigitalStakeout offers a comprehensive dark web monitoring solution that combines data collection, machine learning, security threat intelligence, and workflow automation. With its advanced workflow and alerting features, DigitalStakeout provides maximum flexibility to ensure that important discoveries are promptly flagged and brought to your attention.
Shedding Light on the Dark Web: A Guide to Monitoring and Accessing
ImmuniWeb conducts daily crawls of the Dark Web to quickly identify data leaks and compromised employee credentials resulting from third-party breaches that would otherwise remain hidden and unknown. Our monitoring includes IRC and Telegram channels, social networks, and a free demo of third-party risk, spear phishing, and social engineering. For additional information on Dark Web Monitoring and Access Brokers, take a look at our Tales from the Dark Web CrowdCast.
Encouraging a regular practice of tabletop exercises and red teaming is important for security teams to monitor the dark web. The dark web is a breeding ground for cybercrime where personal data of individuals such as their name, date of birth, social security number, address, and more are gathered and packaged as fullz before being sold off. It is crucial for security teams to stay vigilant and proactive in monitoring these activities to prevent potential data breaches and protect their organization's assets.
Discovering the Secrets of the Dark Web: A Guide to Monitoring
Monitoring the dark web is crucial in protecting personal information from being used for identity fraud or illegal access. Credentials and personal identifiers are at risk in the dark web, making it important for organizations to have a monitoring tool to protect sensitive customer data, valuable intellectual property, and to prevent hacktivists, nation-state actors, or criminal activity. Real-time alerting is also a great feature that allows for immediate response to discoveries and critical information that matches your criteria through the use of monitor or Boolean search criteria.
Dark web monitoring is a crucial aspect of threat hunting. The dark web is a hidden part of the internet where illegal activities such as drug trafficking, human trafficking, and cybercrime take place. Monitoring the dark web allows organizations to stay ahead of potential threats by identifying and mitigating them before they can cause harm. This is achieved by using specialized tools and techniques to search for and analyze data on the dark web. By monitoring the dark web, organizations can protect their sensitive information, prevent financial losses, and maintain their reputation. In today's digital age, it's essential to have a comprehensive threat hunting strategy that includes monitoring the dark web.
Monitoring the dark web has become increasingly important in today's digital age. Cybercriminals are constantly finding new ways to exploit vulnerabilities in software and systems, allowing them to install additional code and gain access to sensitive information. With numerous data breaches occurring over the years, it's likely that everyone's personal information has been compromised and is available for sale on the dark web. To protect oneself from potential cyber threats, it's crucial to utilize tools such as Sticky Password to secure online accounts and prevent unauthorized access. Download Sticky Password for free and join the millions of individuals already safeguarding their online identities.
Discovering the Hidden World: A Guide to Monitoring the Dark Web
Monitoring the dark web is an essential measure to detect potential data breaches and monitoring dark web accidental data leaks. The dark web is a hub for buying and selling various stolen data, illegal goods, and contraband, all while maintaining anonymity and avoiding consequences. As an experienced copywriter, I have tried and tested various password managers to ensure the security of my own data.
The monitoring of the dark web is crucial in today's digital landscape. Unfortunately, these systems are often utilized for malicious purposes, such as aggressive crypto-mining. This can result in a significant drain of CPU power and electricity, which can come at a great cost to the victim. In fact, according to the CrowdStrike Security Cloud, 62 of all detections in the fourth quarter of 2021 were malware-free. So, what does it mean if your information is found on the dark web?
Explore further
Distributed by Исанбай, LLC.