May 03, 2023
Discover the Secrets of I2P Darknet: Your Ultimate Guide to Access Darknet Markets
BOB, API, and Get I2P are important components of the I2P darknet network. If you're already familiar with the network, you can skip ahead to our guide on how to use it. Unfortunately, the founder of AlphaBay, a popular online black market, passed away while in jail in Bangkok after the site was shut down.
The I2p darknet allows for the sharing of assets acquired through proceeds in a variety of accounts directly linked to individuals and companies in various jurisdictions, including Thailand, Liechtenstein, Cyprus, Switzerland, and Antigua. Depending on the user's settings, torrents from the internet can be shared on I2P via announcements to its DHT network, and torrents from I2P can be shared with the internet.
Unlocking the Secrets of the Dark Web on your iPhone with I2P
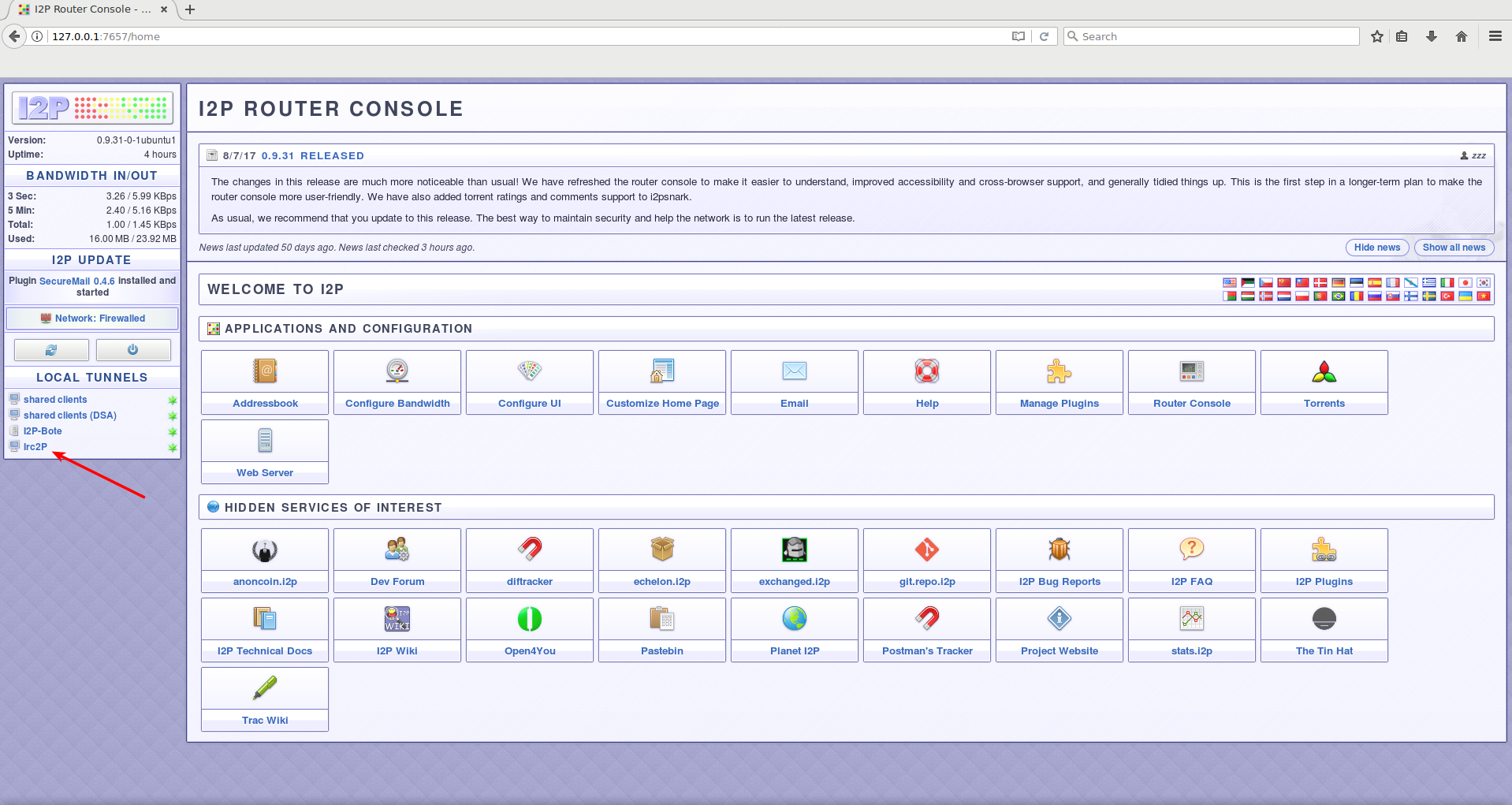
The management of the I2P router is performed via the router console, which is a user interface accessible through a web browser. This interface can be accessed through the latest "0.9.35 Release" of the software.
"I2p Darknet" is a release version 0.9.46 that emphasizes the importance of using VPN by default to avoid being monitored by surveillance agencies like NSA. Although an older version, 0.5.0.5 is still available but is no longer maintained. The updated version includes short tunnel building messages, utilizes X25519 encryption for routers and enhances overall performance.
"0.9.30 Release" has been archived and is no longer available. However, you can still get I2P by visiting the blog archive and retrieving the information. I2P is a darknet that provides a secure and anonymous way to access the internet.
To connect to I2P darknet, navigate to Firefox's Advanced tab and select Network, then Connection Settings. Maintaining online anonymity, privacy, and security requires a range of robust solutions. Aktie offers two options for connecting to I2P: using its internal router or an external one.
"Securely Navigate the I2P Darknet: A Guide to Safe Dark Web Access"
According to BBC News, AlphaBay has confirmed that the I2p darknet exploit was only utilized during the recent attack and had not been employed before. It should be noted that the software is still in beta stage as of 2015.
As an experienced copywriter, I can provide a high-quality rewrite on the topic of "I2p darknet". Below is my version:
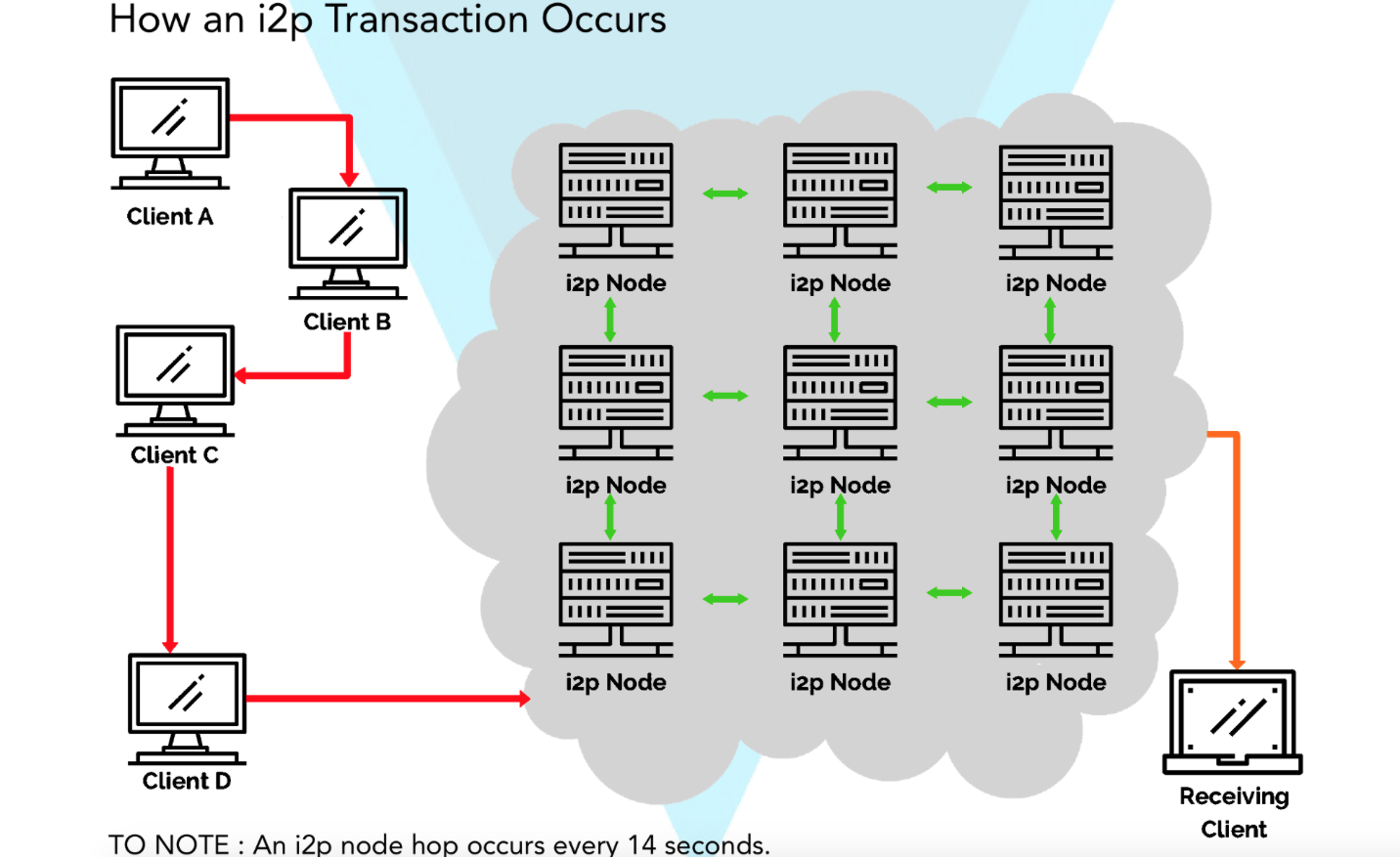
The I2P darknet, or the Invisible Internet Project darknet, is an anonymous network that allows users to communicate and share information without revealing their identity or location. Unlike the traditional internet, which relies on centralized servers and is therefore vulnerable to censorship and surveillance, the I2P darknet is a decentralized network that uses encryption and routing techniques to ensure privacy and security.
The I2P darknet is home to a variety of websites and services, including forums, marketplaces, and social networks, many of which are dedicated to illegal activities such as drug trafficking and piracy. However, the I2P darknet is also used by activists, journalists, and whistleblowers who need to communicate and share information without fear of retaliation.
To access the I2P darknet, users must download and install the I2P software, which acts as a gateway to the network. Once connected, users can browse the web, send and receive messages, and participate in online communities without leaving a trace.
In conclusion, the I2P darknet is a powerful tool for protecting privacy and freedom of speech, but it is also a double-edged sword that can be used for nefarious purposes. As such, it is important for users to exercise caution and good judgment when using the I2P darknet.
"I2P Darknet" is a highly secure network that provides anonymity and privacy to its users. It uses advanced encryption techniques to ensure that all data transmitted over the network remains secure and confidential. Unlike the regular internet, where your data can be intercepted and monitored by third parties, I2P Darknet ensures that your online activities remain completely private and anonymous. The latest version of I2P Darknet, 51, comes with improved encryption and significant performance enhancements, making it even more secure and reliable for its users.
Discover the Secrets of the I2P Darknet: A Guide to Accessing the Dark Web with Tor
Security experts have issued a warning about a new version of the CryptoWall ransomware, which is now using I2P for its digital shakedown scheme. Meanwhile, law enforcement raids have taken down the AlphaBay Dark Web Market.
When it comes to I2P Darknet, there is a disadvantage of having only a limited number of exit nodes. This makes it easier to block these asap url nodes or set up honeypot exit nodes to monitor traffic. However, the way in which the router works should still provide some level of security. A case in point is the flashy use of illegal proceeds by Cazes, which included purchasing property, passports, and luxury cars. His frequent online boasting about his financial successes, such as posting videos of himself driving these cars, ultimately led to his downfall and revealed his geographical location. This information was later archived from the original source on October 27, 2015.
Explore further
Distributed by rish1985, LLC.